By Anna Collins
Alexa’s Listening… So What?
The number of devices on the IoT network is increasing rapidly, and yet these devices remain to be loosely secured. Consumer ignorance toward IoT security, as well as developers’ apathy toward the topic are the main contributors toward this issue. The rapid advancement of technology in this field means that companies rush to release their software without the necessary security features in place (Secure World). Consumers’ willingness to use this technology without these security measures in place means that companies will continue to release devices with weak security measures as long as they continue to sell. For instance, Amazon Alexa has sold over 100 million devices, despite the on-going discussion that Alexa is listening in on every conversation (Tech Crunch).
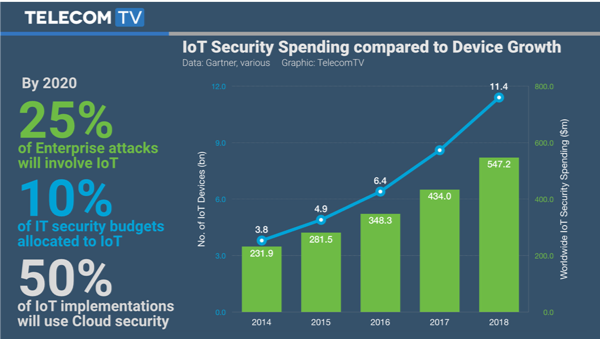
1 Daniels, TTV
As disconcerting as it is that Alexa may be listening to all of your conversations, the situation gets worse. In the context of IoT attacks, an attack could mean that an adversary has access to things such as public infrastructure, like traffic lights (Network World), or internet-connected medical devices (IoT Security Foundation).The lack of security on the IoT network could become an issue far worse than Alexa knowing your favorite songs.
The Mirai Botnet
In 2016, the first attack on the IoT network created cause for alarm about IoT security—or lack thereof. The Mirai Botnet targeted “mainly routers and Internet Protocol (IP) cameras” (SDX Central), shutting down service on Dyn, a DNS provider. This was the first and largest DDOS attack on the IoT network. It quickly demonstrated the impact such attacks could have, when it shut down around 72,000 devices over a 12-hour period (Malware Tech).
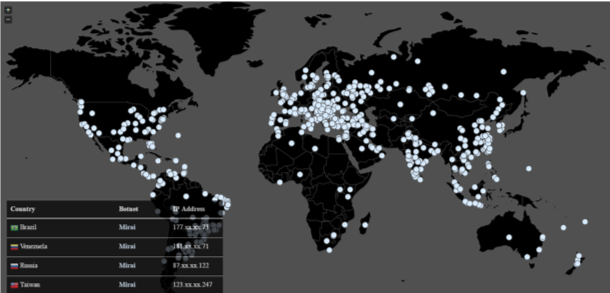
2 Mapping Mirai: Malware Tech
Is Ignorance Bliss?
One of the main problems with IoT security is the lack of public knowledge on the subject. While most individuals understand the bare minimum of computer security—change up your passwords for different websites, keep a passcode on your phone—most people do not understand the idea of securing their IoT devices. Even if most people do understand that their IoT devices must be secured, they do not know how to do so, or how to check that the developer has done so. As Krebs states in his article Some Basic Rules for Securing your IoT Stuff, “…the people who probably need to be reading these tips most likely won’t ever know that they need to care enough to act on them” (Krebs on Security). In this article, he lists tips such as “change your default credentials”, and “update firmware”.
While public ignorance of cybersecurity in general, and especially security of IoT devices is a larger problem in itself, it is not something that can be quickly solved through guidelines and laws. Because of this ignorance on the part of the public, developers must secure the devices that they are releasing, but this does not always happen as it should.
Why Companies Should Care…
Companies have, up until now, attempted to develop devices quickly, even if that meant compromising security standards in these devices: releasing new technology means more money for the company, because consumers don’t seem to care (or understand) when something is under-secured. However, CTIA, the Cellular Telecommunication Industry Association, has released a Cybersecurity Certification Program that just last week certified its first device (CTIA). The HARMAN Spark was the first device to be certified. The Program ensures that “cellular-connected devices have appropriate security capabilities” (CTIA). With any luck, the CTIA Certification will become the standard, and motivate companies to comply with the 16 certification guidelines. Consumers have a role in this—if they refuse to buy devices that are not certified, companies will have no choice but to begin developing compliant devices.
Whose Responsibility is IoT Security?
At the end of the day, consumers have the responsibility to keep up-to-date on security standards and actions that they should be taking to ensure that their devices are secure. Although security is moving in the direction of company’s responsibility, security is not yet universal in these devices. In the meantime, consumers must stay up-to-date on IoT security and make sure that their devices are well secured.
Works Cited
“CTIA IoT Cybersecurity Certification Program Certifies First Device.” CTIA, CTIA, http://www.ctia.org/news/ctia-iot-cybersecurity-certification-program-certifies-first-device.
Daniels, Guy. “Improving IoT Security with Smart Edge Devices.” TelecomTV, TelecomTv, 15 June 2016, http://www.telecomtv.com/content/iot/improving-iot-security-with-smart-edge-devices-13673/.
Eastwood, Gary, and IDG Contributor Network. “5 Of the Biggest Cybersecurity Risks Surrounding IoT Development.” Network World, Network World, 27 June 2017, http://www.networkworld.com/article/3204007/5-of-the-biggest-cybersecurity-risks-surrounding-iot-development.html.
Krebs, Brian. “Krebs on Security.” Krebs on Security, 18AD, krebsonsecurity.com/2018/01/some-basic-rules-for-securing-your-iot-stuff/.
“Mapping Mirai: A Botnet Case Study.” MalwareTech, 5 Oct. 2016, http://www.malwaretech.com/2016/10/mapping-mirai-a-botnet-case-study.html.
Matney, Lucas. “More than 100 Million Alexa Devices Have Been Sold.” TechCrunch, TechCrunch, 4 Jan. 2019, techcrunch.com/2019/01/04/more-than-100-million-alexa-devices-have-been-sold/.
“Medical IoT – A Call to Action.” IoT Security Foundation, http://www.iotsecurityfoundation.org/medical-iot-a-call-to-action/.
Sussman, Bruce. “16 Points of Cybersecurity: The New IoT Device Security Certification Program.” Cybersecurity Conferences & News, 23 Aug. 2018, http://www.secureworldexpo.com/industry-news/internet-of-things-security-certification.